Tailscale vs SSH tunnels
When I first set up the shed network, I was looking forward to having a fixed IP address so that I would at least have the option of not putting everything on AWS. Being able to self-host testing environments isn't critical, but it is a lot more convenient for a small operation like SmartShepherd. I did a post on it a while back but things got wildly out of hand after that.
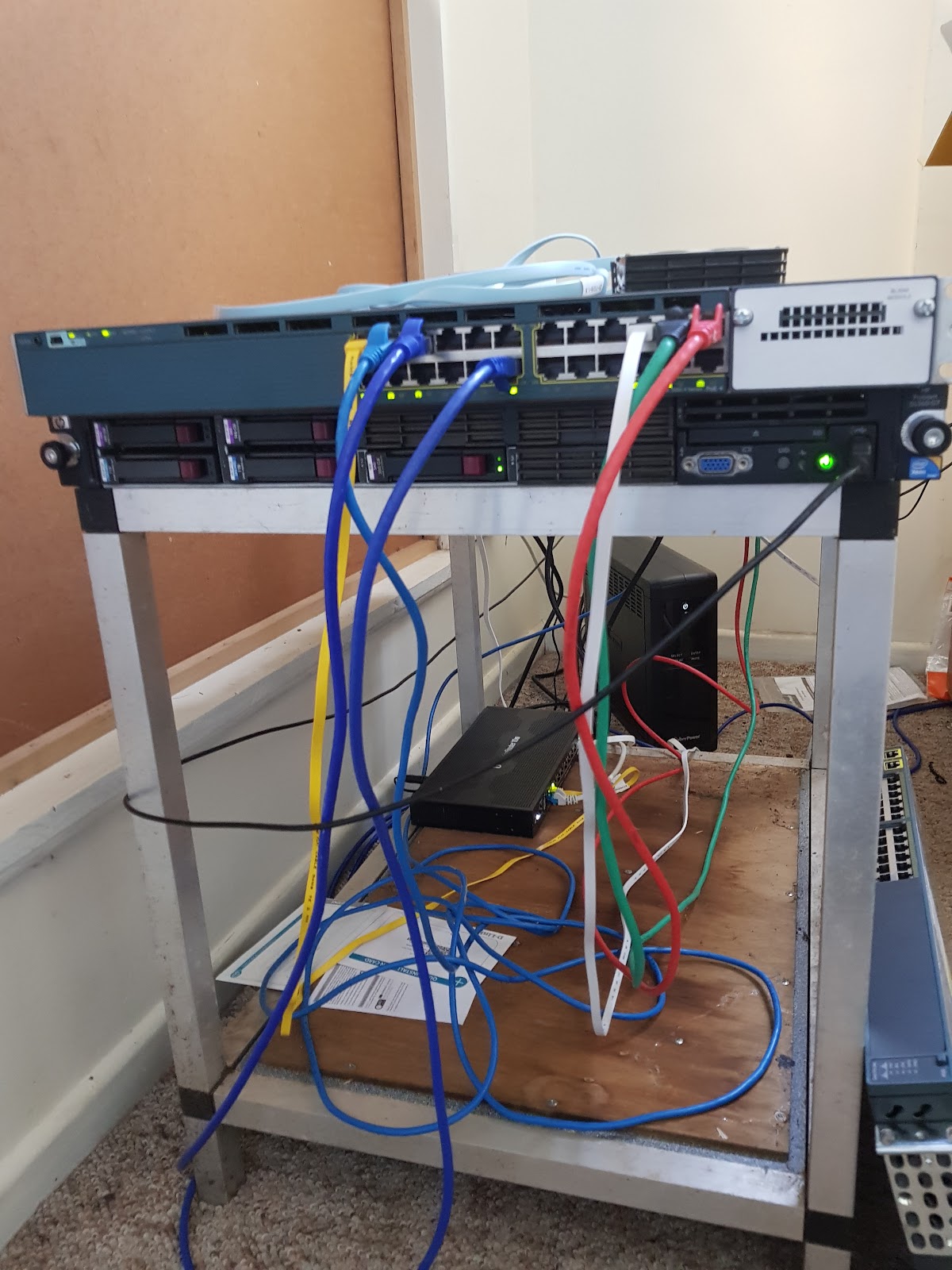
How wildly out of hand? Look at my awesome server rack:
Yeah OK, start ragging on me about my selection of patch cables. The awesome Cisco 3560X switch might only be 1Gb, but it supports switchable Power Over Ethernet and cost me a grand total of $160. Beulah, the HP Proliant server underneath is the guts of the test operation. In the background is the Ubiquiti router and a UPS.Security
About 40 seconds after setting up the Ubiquiti router on the National Broadband Network (NBN) fibre connection and opening up port 22 to be forwarded to my lab server, it started getting hammered with SSH login attempts. A quick analysis of the logs showed most of it coming from Russian or Chinese addresses. Some also from Australia and the US too, but nowhere near as much. I am not sure what exactly people are after on some tiny companies network, but there you go. A google of the issue revealed the security community is somewhat split over what to do about this problem. Using certificates instead of a login for SSH is best practice, a more contentious recommendation was to simply map some other port to your SSH server. This is what I did and the amount of weird login attempts dropped to exactly 0.
From home, I could access the servers, test database and test VMs by simply using the normal ssh client in WSL2 and mapping whatever port I needed to a local port. It worked well, but as time went on and my test setup ambitions grew, I needed more port access and SSH, while working, just didn't scale.
I want a VPN...I think
When I do client customer work, they often provide a VPN solution for access to their machines. The most popular one (Forticlient) is absolute garbage. It insists on running "security scans" at odd times of the day and makes itself extremely difficult to uninstall by disabling the uninstall button in your apps. A lot of VPN clients chop off access to your local network completely, which is really inconvenient. I don't think I've ever found one that I liked. The consumer ones (ExpressVPN, NordVPN etc) have addressed some of those issues but Forticlient is lagging well behind those. The only real solution for running Forticlient is build a dedicated Windows VM and install it in there.
When it came to my own network, one thing I wanted to completely avoid is anything as intrusive as Forticlient. I figure that is a good solution for a big corporate who need to keep their employees machines locked down, but for a small operation it's just too stupid and expensive to contemplate. After some research, I decided that I wanted a WireGuard based solution but I am wary about becoming a full time system administrator when I have other work to do. Enter Tailscale - it gets mentioned positively a lot on Hacker News and generally I find that encouraging.
Is that all there is?
I registered with Tailscale and then promptly forgot about it as other work jumped the priority of securing my network. After a couple of days they sent me a gentle reminder email, so I went ahead and downloaded the tailscale client, set it up as a subnet router and went home to test it out.
Installation of the windows client was uneventful. Once it was working, I tried running up my test environment that connects to a Maria database on Beulah and it worked beautifully. At this point, that was all I needed to do. Using Tailscale, I can RDP to the couple of Windows VMs running on my server, fiddle around with Docker, get access to Chungus the development workstation for when I have forgotton to git commit etc. It's stuff I could do over SSH and tunnels, but using a single Tailscale subnet router gives me access to all of it with a single button press on the app. I have since disabled the ports for SSH on the Ubiquiti altogether. I can work from my study exactly like working in person in the shed. I'm not 100% certain it's more secure than the SSH setup, since I have merely shifted my attack surface from the local router to Tailscale, but it's certainly more convenient.